
Secure your everything
Any cloud. Multi-cloud. From the cloud.
Check Point Software Technologies Ltd. is a leading provider of cyber security solutions to governments and corporate enterprises globally.
Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks. Check Point offers multilevel security architecture, “Infinity” Total Protection with Gen V advanced threat prevention, which defends enterprises’ cloud, network and mobile device held information. Check Point provides the most comprehensive and intuitive one point of control security management system. Check Point protects over 100,000 organisations of all sizes.
Check Points solution portfolio is broken down into 3 key areas.
CloudGuard
Secure the Cloud with a unified cloud native security platform, automating security posture at scale, preventing advanced threats and giving you visibility and control over any workload across any cloud.
Harmony
Protect remote users’ devices and access. Wherever you connect from, whatever you connect to and however you connect – your devices, your privacy and your organisational data secured and protected.
Quantum
Protect your enterprise network from the most sophisticated cyber-attacks with the highest caliber of security, real-time prevention and the world’s highest performing security gateways.
CloudGuard
Check Point cloud native security, delivered through CloudGuard, provides automated security and advanced threat prevention to protect your cloud assets and workloads from the most sophisticated cyber-attacks. Secure your cloud and workload environment with one unified cloud native security platform—automate security posture management, gain visibility of threats, and control your workloads across clouds.
Unified Security for Multi-Cloud
CloudGuard unifies cloud security to provide intelligent threat prevention. Securely protect and prevent threats across AWS, Azure, Google, VMware, IBM Cloud, Oracle Cloud, Alibaba Cloud, Kubernetes, etc all from one platform. Provide centralised visualisation for all of your cloud traffic, security alerts, assets and auto-remediation all from one platform.
Security and Posture Management
Through High Fidelity Posture Management, CloudGuard delivers zero trust, multi-layer, advanced threat prevention, leveraging enriched intelligence with the highest levels of intelligence inputs, in context.
In addition, with its comprehensive compliance and security engine, CloudGuard prevents critical security misconfigurations, and ensures compliance with more than 50 compliance frameworks and best practices.
Automated DevSecOps
CloudGuard allows organisations to shift-left for DevOps to seamlessly evaluate security posture, configuration, and governance during CI/CD. Seamlessly scale and deploy your security in real-time through integration with tools like CloudFormation and Terraform, and evaluate posture pre-deployment to scale across thousands of assets. Automatically define applications security profiles and enforce zero trust boundaries between workloads.
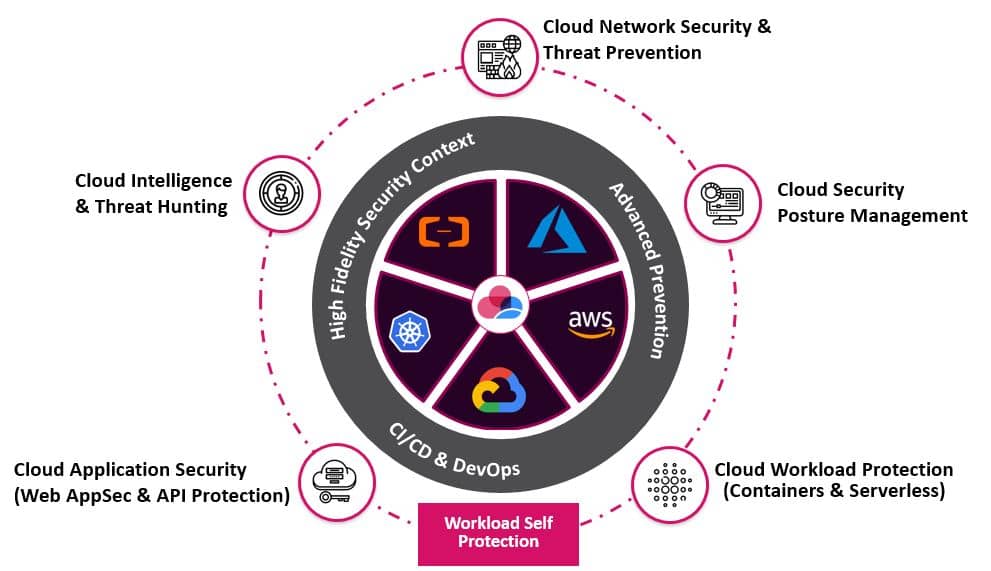
Cloud Network Security
CloudGuard Public Cloud Network Security provides advanced threat prevention and network security through a virtual security gateway—automated and unified across all your multi-cloud and on-premises environments. CloudGuard provides cloud native protection with the industry’s highest security effectiveness, and supports rapid deployment, agility and automation of CI/CD workflows. Create consistent policy to manage security across on-prem and multi-cloud environments.
Cloud Security Posture Management
CloudGuard Cloud Security Posture Management automates governance across multi-cloud assets and services including visualisation. Through CloudGuard High Fidelity Posture Management visualize and assess security posture, detect misconfigurations, model and actively enforce gold standard policies, in context and with enriched intelligence. Protect against attacks and insider threats, cloud security intelligence for cloud intrusion detection, and comply with regulatory requirements and best practices all from one unified platform.
Cloud Workload Protection
CloudGuard Workload Protection provides seamless vulnerability assessment and runtime protection of modern cloud workloads, including serverless functions and containers—automating security with minimal overhead across your multi-cloud environment. Continuously scan workload environments to increase security posture and provide continuous observability and assessment, with self-protection to continuously evaluate and adapt security posture.
Cloud Web App & API Protection
CloudGuard moves application security closer to the edge of the workload, giving more real-time granular protection than a traditional Web Application Firewalls (WAFs). CloudGuard protects web applications and APIs from the most sophisticated types of threats, with an automated, cloud-native security platform. Where traditional WAFs are built using “one-size-fits-all” rule tables even though no two applications are the same, CloudGuard transcends rule-based security by leveraging the power of AI. Automation is a critical component which ensures that security is maintained even in dynamic app development cycles.
Cloud Intelligence and Threat Hunting
CloudGuard Cloud Intelligence and Threat Hunting provides cloud-native threat security forensics through rich, machine learning visualisation, giving real-time context of threats and anomalies across your mutli-cloud environment. Detect anomalies, activate alerts, quarantine threats, and remediate threats automatically, utilising the largest threat intelligence feed.
Harmony
Highest level of security for remote users.
With remote users connecting to your corporate applications from anywhere, your organisation’s attack surface is increasingly expanding. Check Point Harmony is the industry’s first unified security solution for users devices and access.
It protects devices and internet connections from the most sophisticated attacks while ensuring zero-trust access to corporate applications.
Harmony Endpoint
Complete security solution built to protect user PCs and laptops from today’s complex threat landscape.
- Full Endpoint Protection from the most imminent threats such as ransomware, phishing, and malware.
- Fastest recovery enables you to quickly minimise breach impact with autonomous detection and response.
Harmony Browse
Enable a secure, fast, and private internet browsing experience with the industry’s first in-browser protection to inspect 100% of SSL traffic.
- Prevent malware downloads.
- Prevent phishing attacks and corporate credential reuse.
- Block access to websites deemed inappropriate by company policies.
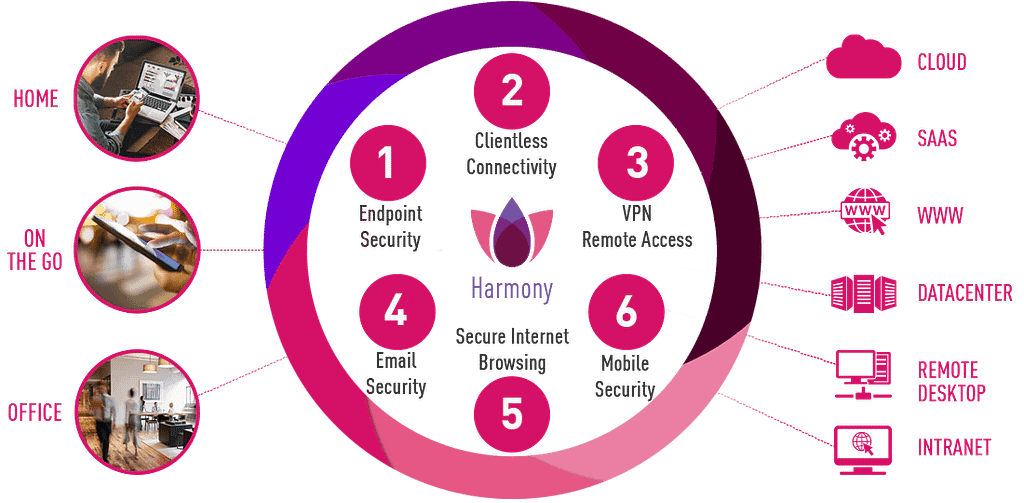
Harmony Email & Office
Complete protection for Office 365 and G Suite.
- Block sophisticated phishing attacks.
- Block malicious attachments while providing safe & clean versions within seconds.
- Prevent sensitive business data leakage (DLP).
Harmony Mobile
Securing employees’ mobile devices to keep corporate data safe across all attack vectors.
- Comprehensive protection across applications, network, OS & device vulnerabilities.
- Simple Management: Harmony Mobile fits perfectly into your existing mobile environment by deploying and scaling quickly.
- User Friendly: protects devices with no impact on user experience or privacy.
Harmony Connect
Harmony Connect is redefining the Secure Access Service Edge (SASE) by making it easy to connect any user or branch to any resource, anywhere, without compromising security. Powered by 11 cloud-delivered security services, Harmony Connect offers a secure and fast local connection, anywhere.
- Clientless access – Provides employees and contractors secure and easy access to any corporate application (including web applications, databases, remote desktops, and SSH remote terminals), with simple SaaS-like access from any web browser and any device (even mobile and home PCs).
- Client-based access – Utilises a VPN agent to provide full network-layer access to corporate networks and applications.
For more information on how you can ensure your workforce is secured, see our Secure Remote Working solutions page.
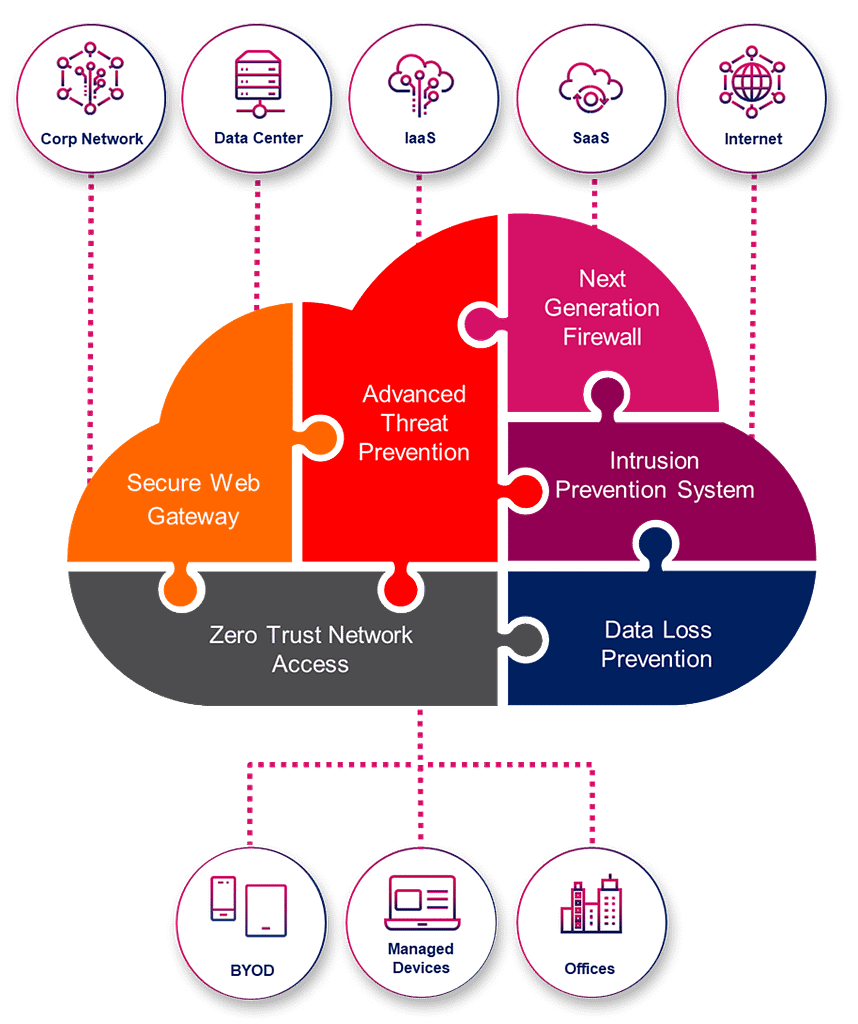
Quantum
Cyber threats are becoming more sophisticated and harder to detect. Check Point Quantum Network Security provides ultra-scalable protection against Gen V cyber attacks on your network, cloud, data center, IoT and remote users.
Check Point Quantum Next Generation Firewall Security Gateways™ combine SandBlast threat prevention, hyper-scale networking, a unified management platform, remote access VPN and IOT security to protect you against the most sophisticated cyber attacks.
Maestro Orchestrator
The Industry’s First Hyperscale Network Security Solution
Allowing to expand from a single gateway to the converged capacity of up to 52 gateways, and reach a threat prevention speed of up to 1.5 Tbps. New high-end models offer a power efficient 1U form factor specifically designed for hyperscale implementations.
Secure Remote Access
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
Cyber Security for IoT
Check Point offers the industry’s most comprehensive cyber security solutions for IoT. Check Points IoT solutions are tailored for different environments, including Smart Office, Smart Building, Industrial, and Healthcare.
Whether you develop IoT devices or deploy them in your organisation, our solutions minimise your exposure to the IoT cyber-risk and prevent the next cyber attack.
Branch Virtual Secure Gateway
Protect your Branch SD-WAN Cloud Connection from cyber attacks. For enterprises that require on-premise branch office security for data privacy, compliance, or location requirements, Quantum Edge can run as a virtual machine (VM) on SD-WAN or universal Customer Premise Equipment (uCPE) devices.
Is your network secure?
Take the test.
Click on the link below to perform a series of network assessments using Check Points ‘Check Me’ program. Test multiple areas of your estate including Network, Endpoint, Cloud and Mobile.
Find out more
If you are interested in learning more about Check Point, wish to book a demo or trial the solution for yourself. Get in touch by clicking the link below.